




Next: C Library Wrapper
Up: TUTTI Reference
Previous: gcov
Contents
Index
Subsections
purify
purifyA run-time memory debugger which pinpoints memory problems at run-time
purify_compiler
purify_compiler is a wrapper for purify dynamic analysis tool. It as
the same interface as the gnu compiler collection (gcc). The compiler
wrapper will compile the source code using the parameters specified at
command line. Insure will instrument the code for dynamic checking of
the software. This results in instrumented binaries that will generate
a purify_ arch
arch _
_ process
process .log files when the code is executed. Warnings
resulting from purify compilation will not be available.
.log files when the code is executed. Warnings
resulting from purify compilation will not be available.
After executing a program instrumented with the purify_compiler,
a log files is generated in the working directory. Although this
log file is human-readable, it is advisable to use purify_scan to
parse the logging and convert it to legible information. See purify_scan(1). This program will also merge double entries in log
files and will filter out the suppressed warnings as specified by
$TUTTI_HOME/etc/purify.suppress.
purify_scan
purify_scan is a script which reads the log files resulting
from a executing purify instrumented source code. The warnings are
extracted and suppressions specified in the suppression file will be
effectuated. Warnings which occur in the purify log files and that are
not suppressed will be issued to the stdout device.
Normally, the output format of purify_scan is he same as the gcc compiler
collection. This format is 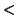 file
file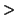 ,
,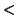 line
line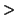 ,
,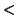 message
message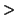 . This
allows the programming to parse the output by an editor. By default, the
warning type (e.g. LEAK_RETURN) is only issued.
. This
allows the programming to parse the output by an editor. By default, the
warning type (e.g. LEAK_RETURN) is only issued.
It is also possible to
generate output in HTML output. Add -html as an optional argument
for this purpose. HTML output will also contain the stack dumps that
where encountered in the logging. Therefor, HTML is recommended for
in-depth analysis of the purify results.
Example
The next piece of code is compiled and linked using purify. We will execute the code three times to
achieve 100
erwinn>> more test.cpp
#include <iostream>
#include <string>
using namespace std;
// GCOV EXPECT 100;
int main ( int argc, const char* argv )
{
cout << "hello nerd" << endl;
switch( argc )
{
case 1:
{
cout << "nice" << endl;
break;
}
case 2:
{
cout << *(new string( "also nice" )) << endl;
break;
}
default:
{
cout << "something is wrong" << endl;
break;
}
}
return 0;
}
erwinn>>
The source code show a memory leak which will show up when adding one command-line argument during.
This error is detected by purify_scan:
erwinn>> purify_compiler test.cpp
Purify 2002a.06.00 Solaris 2 (32-bit) Copyright (C) 1992-2002 Rational Software Corp. All rights reserved.
Instrumenting: ccQJPc8A.o Linking
erwinn>> ./a.out
hello nerd
nice
erwinn>> ./a.out first
hello nerd
also nice
erwinn>> ./a.out default first
hello nerd
something is wrong
erwinn>> purify_scan
test.cpp,20: 4 bytes leaked at 0x84fd0
Verdict : fail
erwinn>> ls
a.out a.out_purify_23632.log test.cpp
a.out_purify_23629.log a.out_purify_23635.log
erwinn>>
As demonstrated by this example, purify generates a new log file for each run. purify_scan merges the several log files and
shows the real memory leak that was detected.





Next: C Library Wrapper
Up: TUTTI Reference
Previous: gcov
Contents
Index
2004-05-28